Introduction
Recently, the University of Toronto decided to switch its Learning Management System (LMS), Blackboard Learn [1] by Blackboard Inc., to Canvas [2] by Instructure. The newly installed LMS is named Quercus, a branded instance of Canvas built for the University of Toronto. This change in software sparked questions for the Digital Tattoo team to find out:
- What happens when public institutions, such as universities, decide to partner with private corporations to provide vendor solutions for its operation?
- What factors are considered or prioritized in this decision?
- What are the relationship and agreements between these vendors and the student end-users of their product?
To address these questions, Digital Tattoo team members Jason and Dominique sat down with Avi Hyman, the current Director of Academic & Collaborative Technologies (ACT), to receive references to many resources for research and to find out the relationship between students and the enterprise software they use at school.
What Determines How Software is Used at School?
When undergraduate and graduate students apply for a program at the University of Toronto for the first time, they agree to a Privacy Policy [3][4] that states the following:
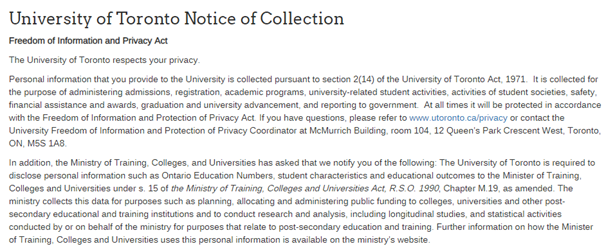
“The University of Toronto respects your privacy. Personal information that you provide to the University is collected pursuant to section 2(14) of the University of Toronto Act, 1971. It is collected for the purpose of administering admissions, registration, academic programs, university-related student activities, activities of student societies, safety, financial assistance and awards, graduation and university advancement, and reporting to government agencies for statistical purposes. At all times it will be protected in accordance with the Freedom of Information and Protection of Privacy Act.”
For undergraduates, this is stated on an information page for perspective students [5] , under the ‘University of Toronto Notice of Collection’ section. In addition, undergraduate students applying to any university in Ontario must also agree to a separate privacy policy with the Ontario Universities Application Centre (OUAC) that govern how OUAC handles and transmits the details of university applications to the respective institutions [6] .
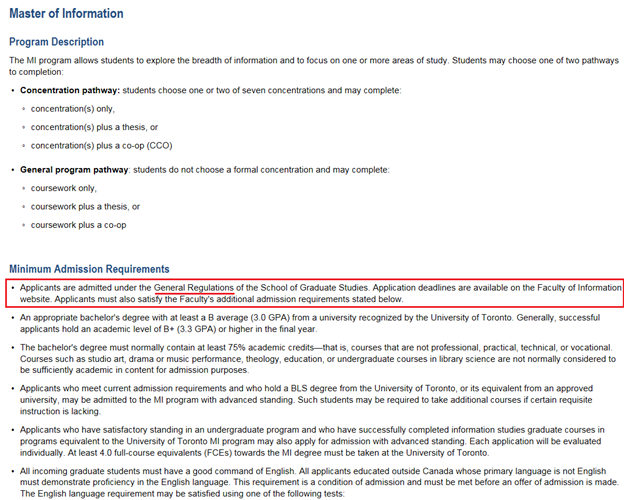
For graduate students, they apply directly to the university through an online application form. The application form for the program that Dominique and Jason are enrolled in, the Master of Information [7] , states that:
“Applicants are admitted under the General Regulations of the School of Graduate Studies.” [8]
Within the General Regulations, it is stipulated that graduate students must also adhere to the Policies and Guidelines listed on the School of Graduate Studies’ website [9] , and in section 11.11 and 11.13, stipulates the Policy on Official Correspondence with Students and the Appropriate Use of Information and Communication Technology [10] . Therefore, the behaviour of students when using institutional software is bound by the policies and agreement between themselves and the university, and not between themselves and the vendor that produced the software.
The guideline for Appropriate Use of Information and Communication Technology states that students, both undergraduate and graduate, must follow the Student Code of Conduct [11] and prohibits activities such as threatening other students, plagiarism, cyberbullying, and using school software for malicious activities like hacking or tricking other people.
How does the School Procure Software for Students to Use?
The University of Toronto has a Procurement Policy that lays out the process of bidding, evaluation, and selection of potential vendors [12] . For Information and Communication Technology (ICT) solutions, Information Technology Services has additional requirements for vendors to fulfill, including the Information Risk Management Questionnaire (IRMQ) [13] and Information Safety Guidelines [14] . The IRMQ evaluates the purpose, storage, retention, threat, and risk levels of information collection of proposed vendor solutions for the ICT to review.
Lastly, the initiative to procure a new vendor solution for the university’s LMS , the Academic Toolbox Renewal Initiative, published their own list of common criteria they established for the potential solutions [15] , with the first criteria listed as “Information Risk, Security, Privacy”. If vendors are able to fulfill all of these requirements of the procurement process, they have the possibility of becoming shortlisted or selected as the winning proposal for procurement.
This type of software license agreement is known as volume or enterprise licensing, where a collective agreement governs the end user license agreement for all members of an organization, instead of a collection of individual licenses for each user [16] . This type of licensing is not unique to educational institutions like universities. In fact, volume or enterprise licenses are commonly used in corporate settings, in which a large number of users require access to a software tool for business operations. In both cases, the organization itself is the signatory to the license, not the end users of the software. Likewise, if a new employee were to use software at the office, they would not be presented with the opportunity to click ‘I Accept’ on a terms of service pop-up before using the software.
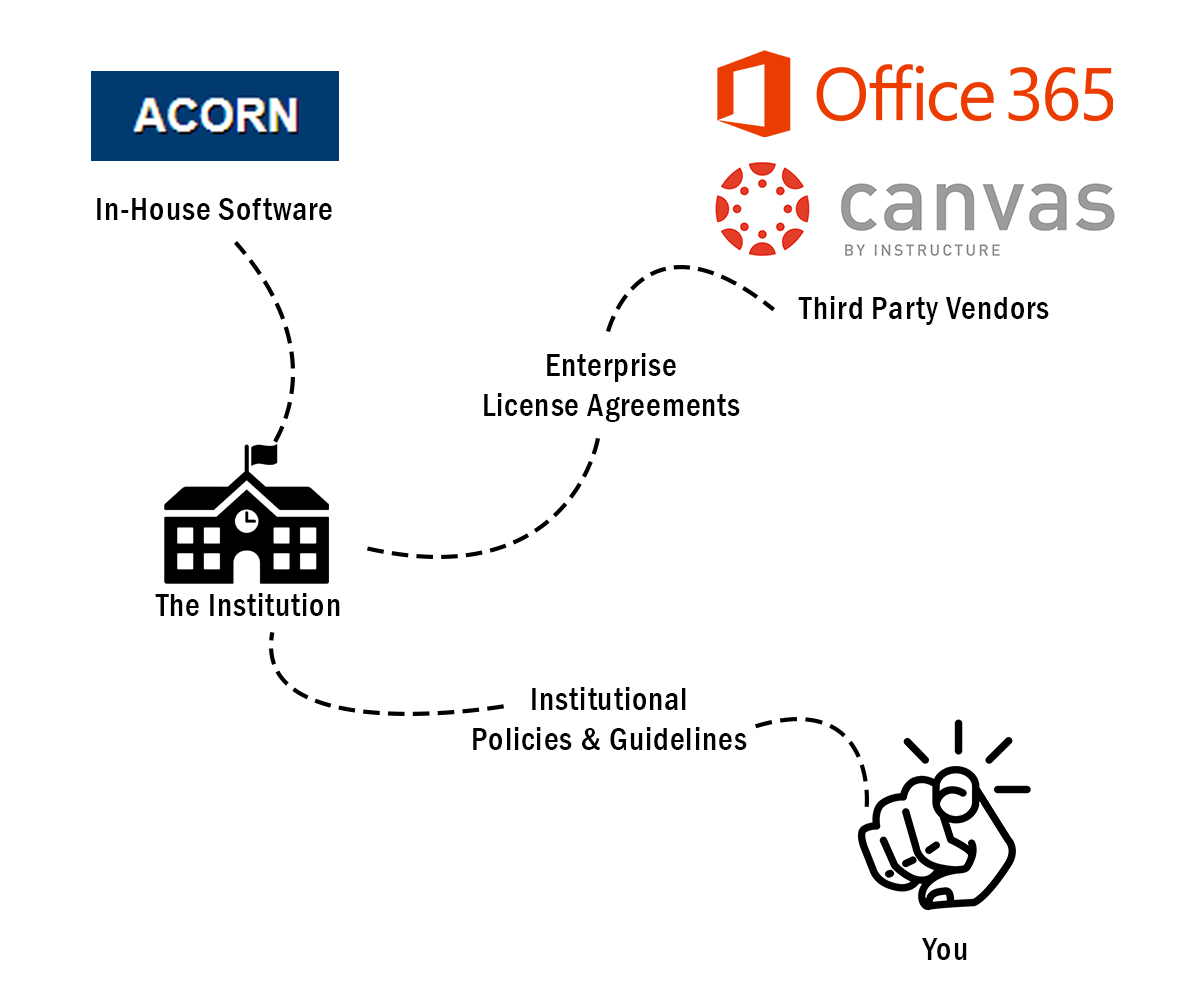
A distinction between user content and user data must be made to clarify how the University of Toronto keeps the information of students safe when partnering with third party vendors. User content consists of the documents, media (photos and videos), and text that you submit and receive from an application. In the case of Quercus, it would include information such as the .pdf file uploaded as an assignment submission, the image attached to a message to a classmate, or the text in the announcements from teachers. Conversely, user data consists of the information generated by a server in order to process interactions between the end-user and the system the person is trying to use. Examples of this data include log-on times, the IP address of the end-user, and the page requests and responses between the user’s machine and the server.
Within the procurement process, the University of Toronto uses the Information Risk Management Questionnarie (IRMQ) to assess factors such as non-essential information and user content collection, system-generated information collection, license agreement transferability, ownership of created data by the university, collection of personally identifiable information, information retention and disposal, software security, and system requirements of potential vendor solutions. This checklist is used in conjunction with the University’s Procurement Policy and Policy on Information Security and the Protection of Digital Assets [17] . In the Policy of Information Security and the Protection of Digital Assets, it states:
“It is the obligation of all University community members to protect information that is created by them and stored by the University and its authorized delegates to its defined principles and standards.”
Furthermore, during the procurement process, the University also audits potential license agreements for FIPPA (Freedom of Information and Protection of Privacy Act) compliance [18]. According to the University’s statement on FIPPA [19] , students are free to request access to these types of records from their university:
- those containing your own personal information;
- most university administrative records;
- records about the subject matter or amount of funding of University research;
- records of University staff employment expenses.
In cases where a student disagrees with the University’s choice of vendor partner for a solution that is for a purpose under the Privacy Policy, the student can contact their student council, their faculty, or the Office of the Provost [20] to raise their specific concerns about any vendor software that is used during their time at the school.
What Does This Mean for You?
Now that you have a better understanding of the agreements between students, the school, and third party vendors, we’re interested in your thoughts about the following. Tell us your answers, and read the responses of other students to these questions in the comment section of this article!
- What do you think about your relationship with the software provided by your academic institution?
- What software do you use most often to complete your coursework or register for courses?
- Were you aware of the agreements that govern how students use software at your school?
- Are you aware of what kinds of information are being accessed by third party vendors to provide their services to you?
- How do you feel when new software is introduced to students?
- What impacts do the decisions in software now mean for students applying to the school in the future?
Appendix
ACT [21] is a partnership between the Center for Teaching Support and Innovation (CTSI) [22] and the Information & Technology Services (ITS) [23] , and they provide strategic leadership in the development and implementation of information technology services that support the academic mission of the University of Toronto.
Disclaimer: The views and opinions expressed in this article are those of the author and do not constitute legal or financial advice.
Always do your own research for informed decisions.
Image Credits
finger pointing by BomSymbols from the Noun Project
school by David from the Noun Project
Sources / Articles You May Be Interested In
Links within the University of Toronto
http://act.utoronto.ca/ – ACT website
http://teaching.utoronto.ca/ – CTSI website
http://its.utoronto.ca/ – ITS
https://www.procurement.utoronto.ca/about-procurement/uoft-procurement-policy – Procurement Policy
http://www.governingcouncil.lamp4.utoronto.ca/wp-content/uploads/2016/03/p0302-pisatpoda-2015-2016pol.pdf – Policy on Information Security and the Protection of Digital Assets
http://www.governingcouncil.utoronto.ca/Assets/Governing+Council+Digital+Assets/Policies/PDF/ppjul012002.pdf – Student Code of Conduct
http://toolboxrenewal.utoronto.ca/common-criteria/ – standards / principles of vendors
http://www.its.utoronto.ca/services/67 – information security guidelines / Information Risk Management Questionnaire (IRMQ) (UofT)
https://www.procurement.utoronto.ca/about-procurement/uoft-procurement-policy – prospective suppliers plus checklist
http://www.provost.utoronto.ca/ – Office of the Provost
http://www.provost.utoronto.ca/policy/use.htm – appropriate use of information and communication technology
http://www.fippa.utoronto.ca/ – U of T FIPPA page
https://sgs.calendar.utoronto.ca/general-regulations – School of Graduate Studies General Regulations
Other Links
https://www.canvaslms.com/security – Canvas encryption page
https://ts.tulane.edu/content/software-license-types – Types of Software Licensing
https://www.utfa.org/content/letter-provost-about-email-migration – UTFA’s Letter to the Provost about Email Migration (Office365)

